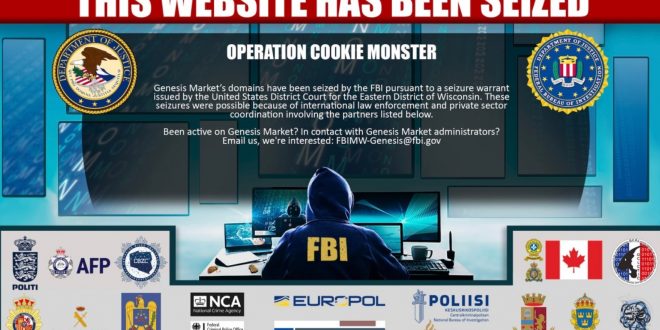
The renowned hacker marketplace Genesis Market, which was used to buy stolen passwords and digital browser fingerprints, has been taken down by American law enforcement.
Although the FBI has not yet made an announcement about the takedown, code-named “Operation Cookie Monster,” Genesis Market domains are currently showing a warning that U.S. law enforcement has carried out a seizure warrant. The notification states, “FBI has seized Genesis Market’s domains in accordance with a seizure warrant issued by the United States District Court for the Eastern District of Wisconsin.”
The notice claims that, in addition to the FBI, law enforcement agencies from the United Kingdom, Europe, Australia, Canada, Germany, Poland, and Sweden participated in the takedown.
The U.K.’s National Crime Agency reported on Wednesday that 200 searches were conducted worldwide and 120 persons were arrested as part of the operation. Two men, aged 34 and 36, who are being held on suspicion of fraud and computer abuse, were among the 19 suspected site users who were detained in the UK, according to the NCA.
Internet users can verify “millions” of email addresses and passwords from the Genesis Market on the data breach reporting website Have I Been Pwned to see if they were affected.
Contacted the FBI, the Department of Justice, and Europol. but hasn’t heard back as of yet.
Genesis Market, an invitation-only internet market that sells cookies, digital browser fingerprints, and passwords taken from infiltrated networks, has been operational since 2017. Attackers could impersonate victims’ browsers to access their online banking and subscription services, such as Amazon and Netflix, without needing the victims’ passwords or two-factor tokens by using these fingerprints, or “bots,” which included IP addresses, session cookies, plugins, and operating system information.
These browser fingerprints would be maintained, according to Genesis before it was shut down, for as long as it had access to a compromised device.
According to Yusuf Arslan Polat, senior threat researcher at Sophos, “Genesis customers aren’t making a one-time buy of stolen information of unknown vintage; they’re paying for a de facto subscription to the victim’s information, even if that information changes.”
The number of infected devices available for purchase on the market was increasing even before its seizure.
According to Cyril Noel-Tagoe, lead researcher at cybersecurity and bot management firm Netacea, “over 20,000 new bots were being added to the site each month in 2021.” “The market experienced a brief decline in the middle of 2022, but despite this, by March 2023, there were over 450,000 bots available for purchase.”
The now-defunct market place has reportedly been connected to millions of financially motivated cyber attacks worldwide. The hackers who broke into gaming major Electronic Arts in June 2021 claimed to have done so by paying $10 for a bot from Genesis Market that allowed them to access a workplace Slack account.
We anticipate an outflow of vendors and customers to rival marketplaces as a result of the seizure of the Genesis Market, Noel-Tagoe tells. Although not on the same scale as the Genesis Market, there are other additional illegal marketplaces that trade logs and credentials. Alternately, a sizable portion of the Genesis Market administrators may split off and launch a different version of the website if they manage to elude police enforcement.
Only a few weeks have passed since the FBI raided the notorious BreachForums hacking forum and detained a 20-year-old New York man suspected of being the site’s operator. It also follows the announcement by US law enforcement last year that SSNDOB, an infamous marketplace where millions of Americans’ personal information, including Social Security numbers, was traded, had been shut down.
 Tech Gadget Central Latest Tech News and Reviews
Tech Gadget Central Latest Tech News and Reviews