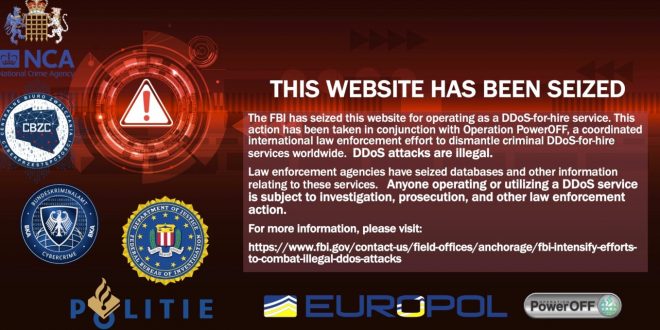
The U.S. has seized 13 more domains linked to popular DDoS-for-hire websites.
These “booter” or “stressor” websites allow admins to stress-test websites. The services actually launch DDoS attacks to take down websites and networks.
On Monday, the DOJ announced that the FBI had seized 13 more domains linked to some of the most prolific booter services as part of Operation PowerOFF, an international law enforcement effort to disrupt online platforms that enable massively distributed DDoS attacks.
The Justice Department said 10 of the 13 domains seized this week were linked to domains seized in a December 2022 sweep that shut down 48 booter services.
The DOJ noted that cyberstress.org appears to be the same service as cyberstress.us, which was seized in December. “While many of the previously disrupted booter services have not returned, today’s action reflects law enforcement’s commitment to targeting those operators who continue their criminal activities.”
Visited 13 FBI-seized websites this week. At the time of writing, Found that at least one of the targeted websites is still operational. The DOJ hasn’t answered questions about why this site keeps loading.
The FBI opened or renewed accounts with each service and launched DDoS attacks against government-controlled computers to investigate the domains, which the DOJ says have “hundreds of thousands” of registered users and have been used to target school districts and government websites. It then monitored these “victim” computers.
The DOJ stated that the test attack was so powerful that it completely severed the internet connection, even though the “victim” computer was on a large network.
In Monday’s announcement, the Justice Department said four defendants charged in December—Jeremiah Sam Evans Miller, Angel Manual Colon Jr., Shamar Shattock, and Cory Anthony Palmer—pleaded guilty earlier this year. These defendants, who will be sentenced this summer, operated the now-defunct “RoyalStresser.com,” “SecurityTeam.io,” “Astrostress,” and “Booter.sx” DDoS-for-hire services.
The UK’s National Crime Agency, Dutch police, and Europol collaborated on the takedowns. The NCA established several DDoS-for-hire sites in the online criminal marketplace earlier this year.
 Tech Gadget Central Latest Tech News and Reviews
Tech Gadget Central Latest Tech News and Reviews